A new methodology that could aid in accurately validating the benefit of quantum computers was recently introduced and evaluated by researchers at NIST/University of Maryland, UC Berkeley, Caltech, and other institutions in the United States. This protocol was published in Nature Physics and is based on a cryptographic method and mid-circuit observations.
“The ultimate driving force behind this research, in my opinion, is whether or not it is possible to effectively validate the computing advantages offered by quantum computers, according to Daiwei Zhu, one of the study’s authors. In other words, how can we use cross-examinations to verify the results of quantum computers if they become more powerful than any classical simulation? This is a problem that almost certainly all of the recent quantum advantage demonstrations are facing. Recent innovations used the concept of cryptographic interactive proof to discover the solution to this problem.
Cryptographic interactive proofs are essentially interactive protocols that let a classical computer check the accuracy of a quantum computer that is much more powerful through a sequence of queries and directives. The techniques utilized by Zhu and his colleagues were first introduced in earlier investigations by scientists from Caltech and UC Berkeley (published in Journal of the ACM and Nature Physics, respectively). Using an ion trap quantum computer, Zhu’s group recently demonstrated these protocols as a proof-of-concept.
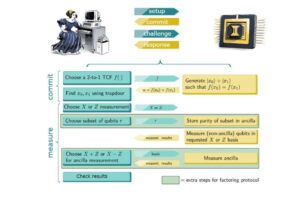
During the interactive calculation, “we divided the qubits into several segments according to their functions (at what stage do they need to be readout),” said Zhu. “We separate the target segments from the other qubits and move them away to perform readout at each readout stage. In this manner, the coherence and quantum data that were previously stored in other segments are kept for use in the remaining calculation.
Zhu and his colleague’s method resulted in readouts of the target segments, or the qubits they were interested in studying. To verify the quantum advantage, these portions were then interactively compared to quantum calculations.
On the one hand, Zhu noted, “we have used long ion chains to integrate mid-circuit measurements into arbitrary quantum circuits with sufficiently high overall fidelity.” “This is applicable to a variety of other interactive algorithms. The efficient proof of the quantum computational advantage, however, is promised by our demonstration when appropriately expanded to bigger systems.
This research team’s new protocols for testing quantum advantage have a number of advantages over other approaches already in use. For instance, their protocol may be implemented with an order of magnitude fewer quantum gate operations than Shor’s method, which is also efficiently verifiable.
The innovative interactive methodology might eventually be used and assessed in more studies. Zhu and his coworkers also intend to develop more interactive methods to evaluate the various facets and dimensions of quantum computing.
Theoretically, we are currently interested in adapting interactive protocols to other jobs including certifiable random number generation, remote state preparation, and verifying arbitrary quantum computations, said Zhu. We are eager to investigate novel phenomena, such as entanglement phase changes, through experiment employing the mid-circuit measurement capacity, as well as to see coherent feedback protocols, such as quantum error correction, put on display.
